IEEE 802.11 WLAN Security attacks
Posted on |
IEEE 802.11 WLAN Security attacks
Wireless Local Area Networks (WLANs) are cost-effective and desirable gateways to mobile computing. They allow computers to be mobile, cable-less and communicate with speeds close to the speeds of wired LANs. These features came with an expensive price to pay in areas of security of the network.
In this document, we are going to identify and summarize these security concerns. Broadly, security concerns in the WLAN world are classified into physical and logical. This video overviews both physical and logical WLANs security problems. It addresses logical security attacks like man-in-the-middle attack and Denial of Service attacks as well as physical security attacks like rouge APs.
Wired Equivalent Privacy (WEP) was the first logical solution to secure WLANs. However, WEP suffered many problems which were partially solved by IEEE802.1x protocol. Towards perfection in securing WLANs, IEEE802.11i emerged as a new MAC layer standard which permanently fixes most of the security problems found in WEP and other temporary WLANs security solutions.
WLAN Security attacks
1 Logical attacks
1.1 Attacks on WEP
Wired Equivalent Privacy (WEP) is a security protocol based on encryption algorithm called “RC4” that aims to provide security to the WLAN similar to the security provided in the wired LAN. WEP has many drawbacks like the usage of small Initialization Vector (IV) and short RC4 encryption key as well as using XOR operation to cipher the key with the plain text to generate cipher text.
Sending the MAC addresses and the IV in the clear in addition to the frequent use of a single IV and the fact that secret keys are actually shared between communications parties are WEPs major security problems. WEP encrypted messages can be easily retrieved using publicly available tools like WEPCrack and AirSnort.
1.2 MAC Address Spoofing
MAC addresses are sent in the clear when a communication between STAs and AP takes place. A way to secure access to APs and hence to the network is done to deny other users from listening to the communication. Integrity means preserving the accurateness and the correctness of information transmitted between STAs and AP. Any security solution should achieve these three goals together.
The security and management problem becomes huge as more APs are installed in the network. So there is a need to centralize and manage security issues in small WLANs as well as large ones and a need to develop techniques to counter security threats. As WLANs applications like wireless Internet and wireless e-commerce spread very fast, there is a need to assure the security of such applications. Many documents have been written to address WLANs security problems. This video reviews WLANs security problem in both physical and logical aspects and discusses the currently available solutions to these problems.
Here in this video, we will, therefore, discus major threats affecting WLANs security and available security protocols and technologies used to counter these threats to filter accesses based on MAC addresses of the STAs attempting to access the network. Since MAC addresses are sent in the clear, an attacker can obtain the MAC address of authorized station by sniffing airwaves using tools like ethereal or kismet to generate a database of legitimate wireless stations and their MAC addresses. The attacker can easily spoof the MAC address of a legitimate wireless station and use that MAC address to gain access to the WLAN.
Stealing STAs with MAC addresses authorized by the AP is also possible. This can cause a major security violation. The network security administrator has to be notified of any stolen or lost STA to remove it from the list of STAs allowed to access the AP hence the WLAN.
1.3 Denial of Service attack
Denial of Service attacks or DoS is a serious threat on both wired and wireless networks. This attack aims to disable the availability of the network and the services it provides. In WLANs, DoS is conducted in several ways like interfering the frequency spectrum by external RF sources hence denying access to the WLAN or, in best cases, granting access with lower data rates. Another way is sending failed association messages to AP and overloads the AP with connections till it collapses which, as a result, will deny other STAs from associating with the AP.
Attempts are made by researchers to overcome such attack by introducing new network elements like Admission Controller (AC) and Global Monitor (GM). AC and GM allocate specific bandwidth to be utilized by STAs and in the case of heavy traffic on AP, they can de-route some packets to neighboring AP to deter DoS attacks on APs.
Also, attackers try to exploit the authentication scheme used by APs; this will force the AP to refuse all legitimate connections initiated by valid STAs. Little is done so far to counter DoS attacks, the fact that DoS attacks are serious and tools to counter them are minimum attracted attackers to vandalize WLANs using such attacks.
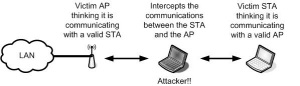
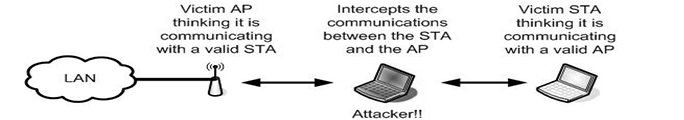
1.4 Man-in-the-middle attack
This is a famous attack in both wired and wireless networks. An illicit STA intercepts the communication between legitimate STAs and the AP. The illegal STA fools the AP and pretends to be a legitimate STA; on the other hand, it also fools the other end STA and pretends to be trusted AP. Using techniques like IEEE802.1x to achieve mutual authentications between APs and STAs as well as adopting an intelligent wireless Intrusion Detection System can help in preventing such attacks.
1.5 Bad network design
WLANs function as an extension to the wired LAN hence the security of the LAN depends highly on the security of the WLAN. The vulnerability of WLANs means that the wired LAN is directly at risk. A proper WLAN design should be implemented by trying to separate the WLAN from the wired LAN by placing the WLAN in the Demilitarized Zone (DMZ) with firewalls, switches, and any additional access control technology to limit the access to the WLAN. Also dedicating specific subnets for WLAN than the once used for wired LAN could help in limiting security breaches. Careful wired and wireless LAN network design plays an important role to secure access to the WLAN.
1.6 Default AP configurations
Most APs are shipped with minimum or no security configuration by default. This is true because shipping them with all security features enabled will make usage and operation difficult for normal users. The aim of AP suppliers is to deliver high data rate, out of the box installation APs with- out sincere commitment to security. Network security administrators should configure these AP according to the organization’s security policy. Some of the default unsecured settings in APs shipped today are default passwords which happen to be weak or blank.
Service Set Identifier (SSID) is the name given to a certain WLAN and it is announced by the AP, the knowledge of SSID is important and works like the first security defense. Unfortunately, by default, some Aps disable SSID request which means users can access the WLAN without proving the knowledge of SSID. On the other hand, Some APs don’t disable SSID request, in fact, the SSID request is enabled but the SSID name itself is broadcasted in the air. This is another security problem because it advertises the existence of the WLAN. SSID requests should be enabled and SSID names shouldn’t be broadcasted so users have to prove the knowledge of WLAN’s SSID prior establishing communication.
Another default configuration in APs is that Dynamic Host Configuration Protocol (DHCP) is ON so users can obtain IP addresses automatically and hence access the WLAN easily. Simple Network Management Protocol (SNMP) parameters are also set to unsecured values. Network security administrators have the responsibility to change these configurations to maximize APs security.
2 Physical attacks
2.1 Rogue Access Points
In normal situations, AP authenticates STAs to grant access to the WLAN. The AP is never asked for authentication, this raises a security concern, what if the AP is installed without IT center’s awareness? These Aps are called “Rogue APs” and they form a security hole in the network. An attacker can install a Rogue AP with security features disabled causing a mass security threat. There is a need for mutual authentication between STAs and APs to ensure that both parties are legitimate.
Technologies like IEEE802.1x can be used to overcome this problem. Network security administrators can discover Rogue APs by using wireless analyzing tools to search and audit the network.
2.2 Physical placement of APs
The installation location of APs is another security issue because placing APs inappropriately will expose it to physical attacks. Attackers can easily reset the APs once found causing the AP to switch to its default settings which are totally insecure. It is very important for network security administrators to carefully choose appropriate places to mount APs.
2.3 AP’s coverage
The main difference between WLANs and wired/fixed LANs is that WLANs relies on Radio Frequency (RF) signals as a communication medium. The signals broadcasted by the AP can propagate outside the perimeter of a room or a building, where an AP is placed, allowing users who are not physically in the building to gain access to the network.
Attackers use special equipments and sniffing tools to find available WLANs and eavesdrop live communications while driving a car or roaming around CBD areas. Because RF signals obey no boundaries, attackers outside a building can receive such signals and launch attacks on the WLAN. This kind of attack is called “war driving”.Publicly available tools are used for war driving like NetStumbler.
Hobbyists also chalk buildings to indicate that signals are broadcasted from the building and the WLAN in it can be easily accessed. This marking is called “war chalking”. In War chalking, information about the speed of the connection and whether the authentication scheme used is open or shared keys are mentioned in the form of special codes agreed upon between war-chalkers. There are a lot of doubts and debates in the wireless network community regarding the legality of war chalking and war driving activities.
Network security administrators can test the propagation of APs by using special tools to verify to what extent the signals can reach. Accordingly, they can control the propagation of APs by lowering the signal strength or by using a smart type of antennas to control the direction of the signal or move the AP to a place where it is guaranteed that the signal will not travel beyond the building premises. Some work has been done in the area of smart antennas in APs to direct the propagation of traffic. Directing the propagation of traffic as well as managing the power of signals originating form the APs can be helpful in restricting the coverage of APs to specified regions.
Sometimes public and open access to the WLAN is preferable, such public WLANs are called “hot spots”. Implementing hot spots is subject to many of the mentioned security problems. It is important to understand that breaking the security of a hot spot will result in breaking the security of wired network connected to that hot spot.
The control and monitoring of APs are minimal because it is installed in a public area like hotel lobbies, coffee shops, and airport lounges so preventing physical access to AP is more difficult as the site has to be monitored all the time. In this case, there is a tradeoff between giving users the mobility and the flexibility to log in to the network in public areas versus the security of the network infrastructure. The network backbone can be highly secured but a breach in the security of the network access node (i.e. AP) can always lead to a breach in the security of the backbone behind the node.
Books you may interested